Confidential Computing with TEEs: Protecting Data in Use
Organizations operating in highly secure environments, such as the governments, military or defense industry, rely on confidential computing as a means to ensure security to all aspects of their operations including end-to-end computation process.
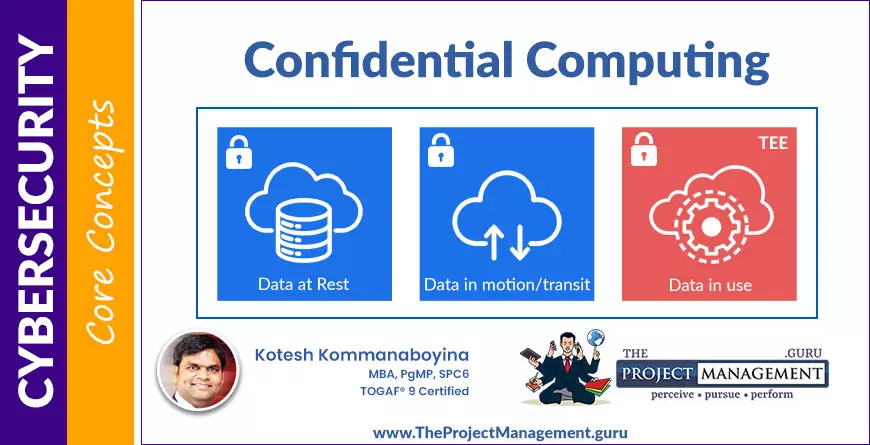
Confidential Computing with Trusted Execution Environments (TEEs)
In a Client/Server computing model, the client requests server to take some action on the client’s behalf – often a request from browser for server-side data.
In the process of serving the client’s request server may have to do the following:
- Access data in a different storage environment
- Perform computation on the data
- Send the processed or refined data to client
Often computing models add a layer of security to the Client/Server request model. Applying encryption strategies to the data on the storage area to restrict unauthorized access from the individuals or processes is termed as protecting data at rest. Adding a layer of security to the network communications to restrict eavesdropping attacks between Client & Server and between Server & Storage is often called protecting data in motion or transit.
Traditionally, computation models ignored adding a security layer for the data that is being actively processed on the server’s memory.
Confidential Computing model insists adding a security layer to protect the code and data being processed in server memory which can be termed as protecting data in use emphasizing the use if TEEs (Trusted Execution Environments)
Trusted Execution Environment guarantee that no outside process can view or alter the data being handled with its’ environment.
What is a Trusted Execution Environment?
Data protection is ensured throughout the entire computation lifecycle with a Trusted Execution Environment which enhances the confidence and assurance of the computation model.
